7 Ways to Defend Your Software Supply Chain
As hackers get more sophisticated and software gets more complex, CISOs need to improve their ability to identify, isolate, and mitigate malicious software attacks. Automation and AI will be their new best friends.
If you’ve been paying attention to network threats over the past few years, you’ve probably noticed a shift. While bad actors still conduct botnets and automated ransomware attacks, they’re putting more energy into big-game hunting – attacking the supply chains that provide the software in use at countless organizations.
The names of these attacks are now infamous – SolarWinds, Kaseya, NotPetya, and 2023’s MoveIT breach, to name a few – and the advantage of targeting the supply chain is obvious: a bigger payoff. Whether hackers compromise an open-source or third-party library through a GitHub repository, find a vulnerability in packaged software, or leverage social engineering to infiltrate a development environment, a single exploit can penetrate hundreds or thousands of private and public networks all around the world.
The SolarWinds attack impacted some 18,000 enterprises; MoveIT, more than 2,500 organizations (and counting), affecting some 67 million people.
Know all your software supply chain vulnerabilities. In seconds.
Juniper Research predicts that by 2026, software supply chain attacks will cost the global economy nearly $81 billion, with the majority of those costs hitting healthcare, finance, government, and automotive industries.
A security leader’s goal is to eradicate vulnerabilities and reduce your attack surface. Compromises to computer networks occur in increasingly insidious (and subtle) ways, from installing trusted software that has been backdoored by an attacker, to neglecting the threats of shadow IT. In the latter case, one careless action of an employee downloading an unapproved installer or freeware can upend months or years worth of security efforts.
So what’s a chief information security officer (CISO) to do? With hackers focused on these high-impact targets, CISOs must be proactive. The standard advice they get is “Trust but verify.” But that assumes trust first and that assumption is becoming increasingly problematic. What I tell CISOs is this: Zero trust – until you verify.
A complex supply chain facing constant threats
Installing software used to be fairly straightforward: You found a vendor you could trust and you downloaded their product. Today the supply chain includes not only the company you bought a license from but also the third-party components that make up the software, the utilities your staff builds and augments in-house, and the software you use on the cloud.
CISOs must be proactive and follow a [new] simple motto: Zero trust – until you verify.
New vulnerabilities in the software supply chain (such as those seen in Apache Struts, OpenSSL, cURL, and other shared utilities and libraries) appear with dismaying regularity. When bad actors package up these compromised codes and insert them into known software, they are exploiting not just a vulnerability but also the trust between supplier and customer that software is “safe.” If a bad actor gets inside the tech a software company uses to sign code as authentic, that malicious code is now out there spreading without people knowing it’s been corrupted.
To make things worse, hackers may also steal signing certificates or developer credentials and use this privileged identity to ensure their malicious intent bypasses your security detections.
Luckily, with the right tools, careful preparation, automation, and a zero-trust-till-verify approach to network architecture, security leaders can learn to quickly identify and neutralize these threats. We suggest following these seven steps:
1. Start with a network inventory
As the saying goes, “You can’t protect what you can’t see.” You need to have the tools, processes, and trained personnel in place that can give you complete awareness of all the devices and software in your organization. An automated endpoint management or protection system can help you protect your attack surface – as long as it’s running on all your endpoints.
Automation can help protect your software supply chain as well. From a numbers perspective alone, there are many more problems, endpoints, and challenges facing individual organizations than there are cybersecurity professionals on staff. In its Cost of a Data Breach 2023, IBM notes that “organizations that used [AI and automation] experienced, on average, a 108-day shorter time to identify and contain the breach,” and saved an average of $1.76 million in lower data breach costs.
AI will also be an ally in this fight. While it is still an emerging technology, there is promising potential in the ways AI – which I often refer to as augmented intelligence – will support security teams to triage faster and with greater overall accuracy.
[Read also: Here’s your ultimate guide to AI cybersecurity – the benefits, risks, and rewards]
Through the use of advanced technology, you can reduce not only the workload that accompanies a response to attacks but also the attendant human burnout – and human error that comes with “alert fatigue.”
2. Put SBOMs to work
One feature of modern software that makes it so readily exploitable is that it is no longer written from scratch. Developers grab snippets of code from third-party online code libraries, and every snippet presents a potential vulnerability. So it’s no longer enough to know what software is on your system; you now need to list every single one of the libraries or modules that has been used to build the software you want to install.
Maintaining an accurate inventory of all the ingredients of all the software on your network would be hard enough if that inventory were static. It isn’t.
This kind of list, referred to as a software bill of materials (SBOM), helps keep track of vulnerabilities in third-party files, libraries, and components. It is useful – and far beyond the ability of humans to manually create.
Ideally, vendors and software creators will embrace their role as the single source of truth for their software and include SBOMs for their software applications. Tools also exist that automate the creation of these lists. And the federal government has also stepped in: President Biden’s 2021 Executive Order on Improving the Nation’s Cybersecurity requires vendors that provide software to the federal government to include an SBOM for everything in their products.
[Read also: The U.S. government’s battle plan to fortify supply chains]
Maintaining an accurate inventory of all the ingredients of all the software on your network would be hard enough if that inventory were static. It isn’t: If software developers download public-source code and change its name or modify it slightly, that download might look different in their software than it does in someone else’s. Or if a GitHub code repository is safe on Tuesday but then an attacker makes a malicious “commit” or alteration to the code on Wednesday, your network is vulnerable again as soon as someone re-imports that repository.
3. Build a software testing environment
If you are building software, you must add another layer of defense with a private repository of any code you’ve implemented. This code should be audited and secured, and never pull directly from original upstream sources without a security review. With a secure repository in place, you can download a piece of software and go through it line by line in private, secure in the knowledge that no one outside of your organization can make changes to it.
If, for example, you want to use the software library OpenSSL, you can grab the source code and bring it into this your private development environment where you can implement patches and upgrades as new versions come out. The advantage of this approach is that it allows you to port over the code and control your reviews of any new code added to it. The repository gives you an opportunity to test the software and make sure that it will not break anything in your environment—before you deploy it.
4. Establish a vulnerability management plan
Even with a test environment, it is likely that some attacks will succeed. You therefore need to create a vulnerability management plan and ask yourself:
- Am I prepared to take action when something gets through? Who will be in charge of the response?
- Do we have the policies and procedures in place to guide how we handle patch management when a critical vulnerability emerges?
- What is our third-party risk management plan: If a third-party library has a critical vulnerability, how will we identify any applications using that third-party library, and how will we take critical services offline to patch it?
[Read also: Supply chain security is tough – so what should good look like?]
- Can we neutralize the attack without significant impact on our business-critical operations?
- Have we established effective communications policies for internal and external stakeholders as part of our emergency remediation plans?
5. Put enforcement teeth into your policies
After so many attacks, CISOs know the importance of training employees to avoid downloading anything from suspicious sites or, say, letting their kids install Minecraft on a work device. And workers are increasingly cautious with internet-of-things (IOT) devices like cameras, printers, and VoIP phones (which use an internet connection and “Voice over Internet Protocol” technology to make calls).
You need to have both a written policy on acceptable software use and a way to technically enforce it. This is not a simple task, but it can be made simpler… with automation.
But a critical layer in any defense is the technical controls that prevent unwanted intrusions from happening in the first place. It’s one thing to tell employees not to install untrusted USB drives or untrusted software into their laptop; it’s another thing to make it technically impossible for them to do so.
This is the layer many companies struggle with. If for no other reason than regulatory compliance, you need to have both a written policy on acceptable software use and a way to technically enforce it. This is not a simple task, but it can be made simpler, once again, with automation. Regularly auditing your “paper policies” and testing whether you’ve created technical enforcements to complement them is an exceptional strategy to mature your organization’s security posture.
[Read also: Why workers violate cybersecurity policies]
6. Conduct a thorough assessment of capabilities
In making plans to prepare for the inevitable supply chain disaster, CISOs would do well to answer the questions posed in this graphic:
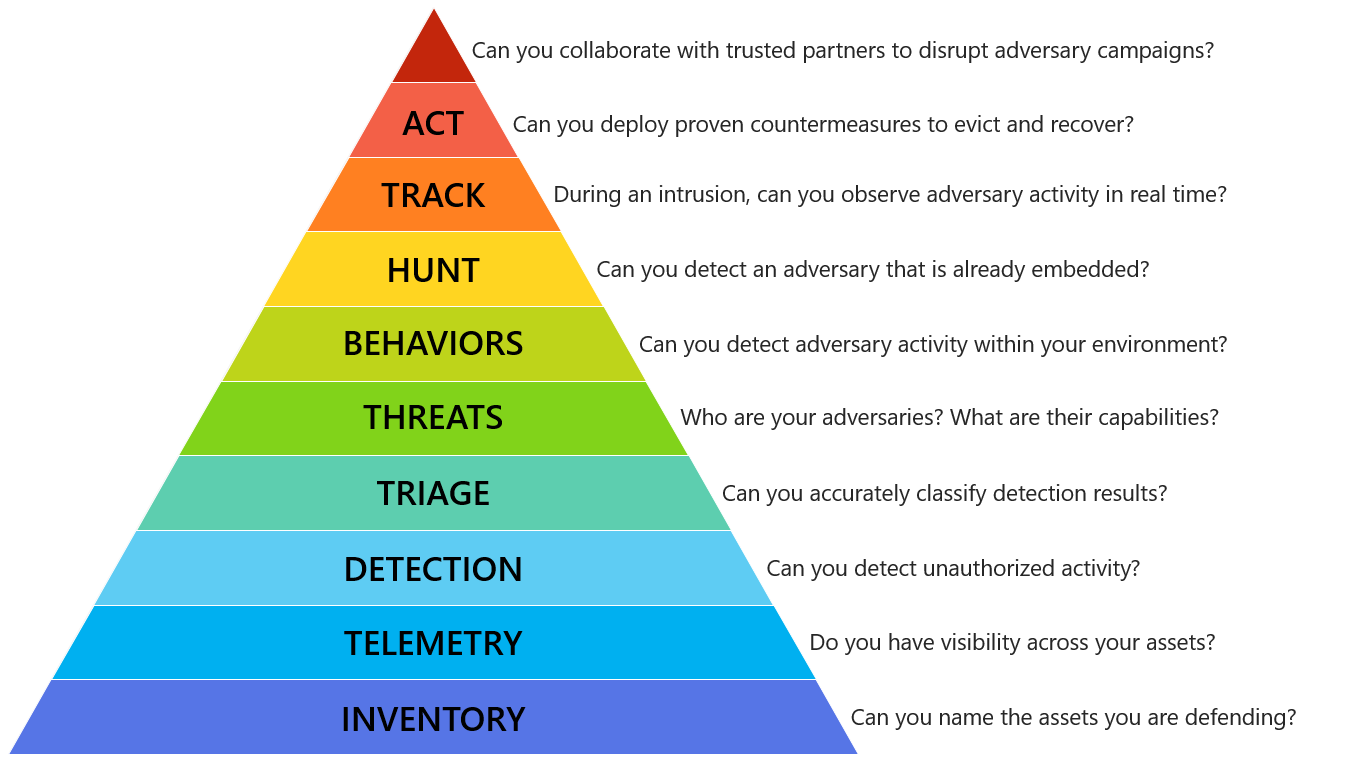 Developed by Microsoft security expert Matt Swann, this graphic represents an incident response “hierarchy of needs.” It is modeled after U.S. psychologist Abraham Maslow’s Hierarchy of Needs, which outlines human needs, starting at the most basic. Swann’s version describes the capabilities that organizations must build to defend their business assets. It, too, starts with the most basic – an asset inventory – and each level serves as a prerequisite for the capability above it.
Developed by Microsoft security expert Matt Swann, this graphic represents an incident response “hierarchy of needs.” It is modeled after U.S. psychologist Abraham Maslow’s Hierarchy of Needs, which outlines human needs, starting at the most basic. Swann’s version describes the capabilities that organizations must build to defend their business assets. It, too, starts with the most basic – an asset inventory – and each level serves as a prerequisite for the capability above it.
Security leaders may need to have difficult internal conversations about where their organizations sit on this pyramid in terms of maturity. Some companies may find themselves stuck at the bottom-most levels, unsure if they can name and ensure visibility into all the assets they are defending. If you can’t name and locate all your assets, everything you do from that level up may be reaching only a portion of your total attack surface, and causing critical hits to your team’s efficiency.
Your threat hunters will be significantly more effective when they’re hunting in an environment with robust telemetry and visibility.
7. Nurture the ecosystem of relationships
In my tenure as director of endpoint security research at Tanium (which owns this publication), I’ve seen customers try to secure their software supply chain with a wide variety of approaches, from homegrown tooling to off-the-shelf solutions. The problem is that, if not done in a thoughtful way, attempts to identify, isolate, and neutralize bad code can slow down or, worse yet, take down an entire system.
A more effective strategy is to nurture relationships among all the stakeholders – across your organization, your vendor network, and your supply chain. CISOs are more effective when they understand how their employees are using technology, how vendors are securing their software, and how government and other industry partners can help support those efforts.
Your software supply chain is made of many links. So is the best plan to protect it.
Matt Swann’s “Incident Response Hierarchy of Needs” chart provided by permission.








