Drilling Down on Data Privacy: 5 Key Charts From ISACA’s 2025 Report
Regulations are pushing more enterprises to build data privacy programs, but researchers were surprised by some of the hows and whys – and why nots – revealed in this new report. We highlight five to guide enterprises in their own data privacy plans.
It’s hard enough finding good cybersecurity talent, but with a growing list of compliance regulations designed to protect consumer information, more organizations are realizing they need skilled pros in yet another critical area: data privacy.
In its fifth annual State of Privacy report, ISACA found organizations understand the value of data privacy — how it plays a role in decreasing data breaches and helps increase both brand reputation and consumer trust. However, the report also revealed that the most common obstacle privacy programs face is the complex legal and regulatory landscape. And there’s the added challenge of teams relying on AI tools to share and protect data.
Despite the important role that privacy departments can play in protecting consumer information, those headcounts aren’t rising — in fact, they’re even down a bit.
“I think the most surprising thing to me is that this year, median privacy-staff sizes were a little bit smaller, eight this year compared to nine [the year before],” said Safia Kazi, privacy professional practices principal at ISACA, during a recent conversation about the ISACA privacy report. Not a huge dip, granted, but it’s just those slight up- and downward ticks of the needle that she monitors to better anticipate longer-term trends.
We’re seeing that a lot more people are using AI for privacy-related tasks.
On the other hand, Kazi added, the news of the understaffing, while surprising, didn’t feel as bad among the respondents as it did last year. One theory as to why? “We’re seeing that a lot more people are using AI for privacy-related tasks,” she said.
Formerly known as the Information Systems Audit and Control Association, ISACA is a global nonprofit professional association and a leading IT certification and training group focused on promoting digital trust. The State of Data Privacy report, which surveyed more than 1,600 security leaders, managers and other IT pros from around the world, covered a broad range of topics. Focal Point and Kazi homed in on five key areas:
1. Getting board buy-in for data privacy
Board Views of Privacy Programs
Do you think your board of directors views your enterprise’s privacy program as:
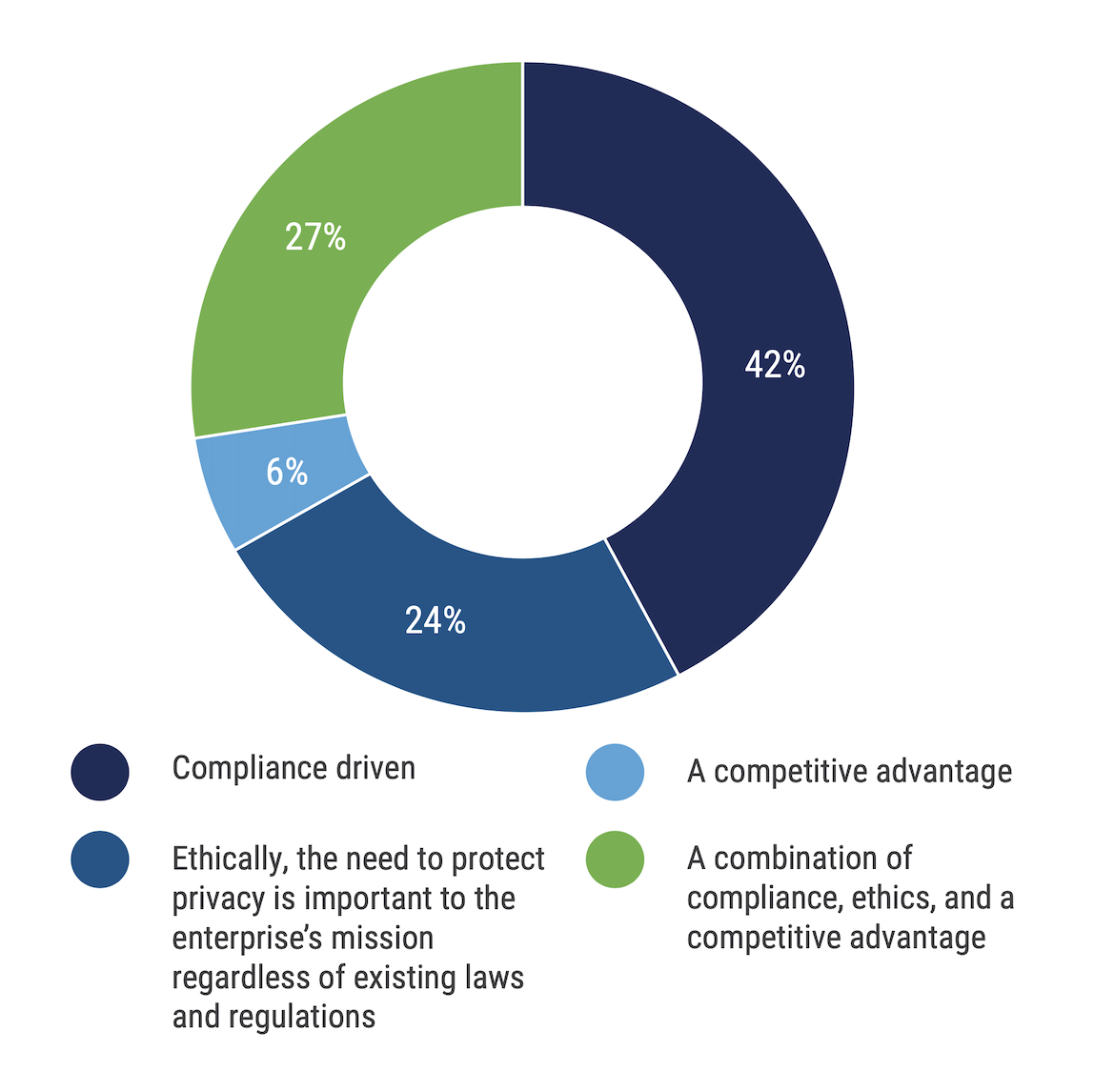
Source: ISACA’s 2025 State of Privacy
The buy-in on data privacy from the board of directors of any organization is vital to meeting the goals of the privacy team. According to the report, boards of directors are backing privacy efforts, with 57% of respondents saying they get adequate backing and 74% saying privacy objectives align with business goals, which haven’t changed much from the 2023 numbers.
Those that were ethically oriented felt more able to be compliant with new laws and regulations [than] enterprises that were purely compliance-driven.
However, most of these boards support data privacy because of compliance requirements, not because they see it as a value proposition.
“Ideally, though, I would hope that organizations can start to think more about why data privacy matters,” said Kazi. “Interestingly, what we found is that enterprises that were purely compliance-driven weren’t actually more confident in their ability to be compliant. We found that those that were ethically oriented felt more able to be compliant with new laws and regulations.”
Those organizations who tend to be ethically oriented take steps to evaluate and analyze their data practices in a way that considers how misuse can have an adverse effect on customers and employees. It is realizing the real-life implications that can come if organizations aren’t adequately protecting data.
2. Data privacy budgets – the arrows point down
Privacy Budget Changes
How will your organization’s privacy budget change in the next 12 months?
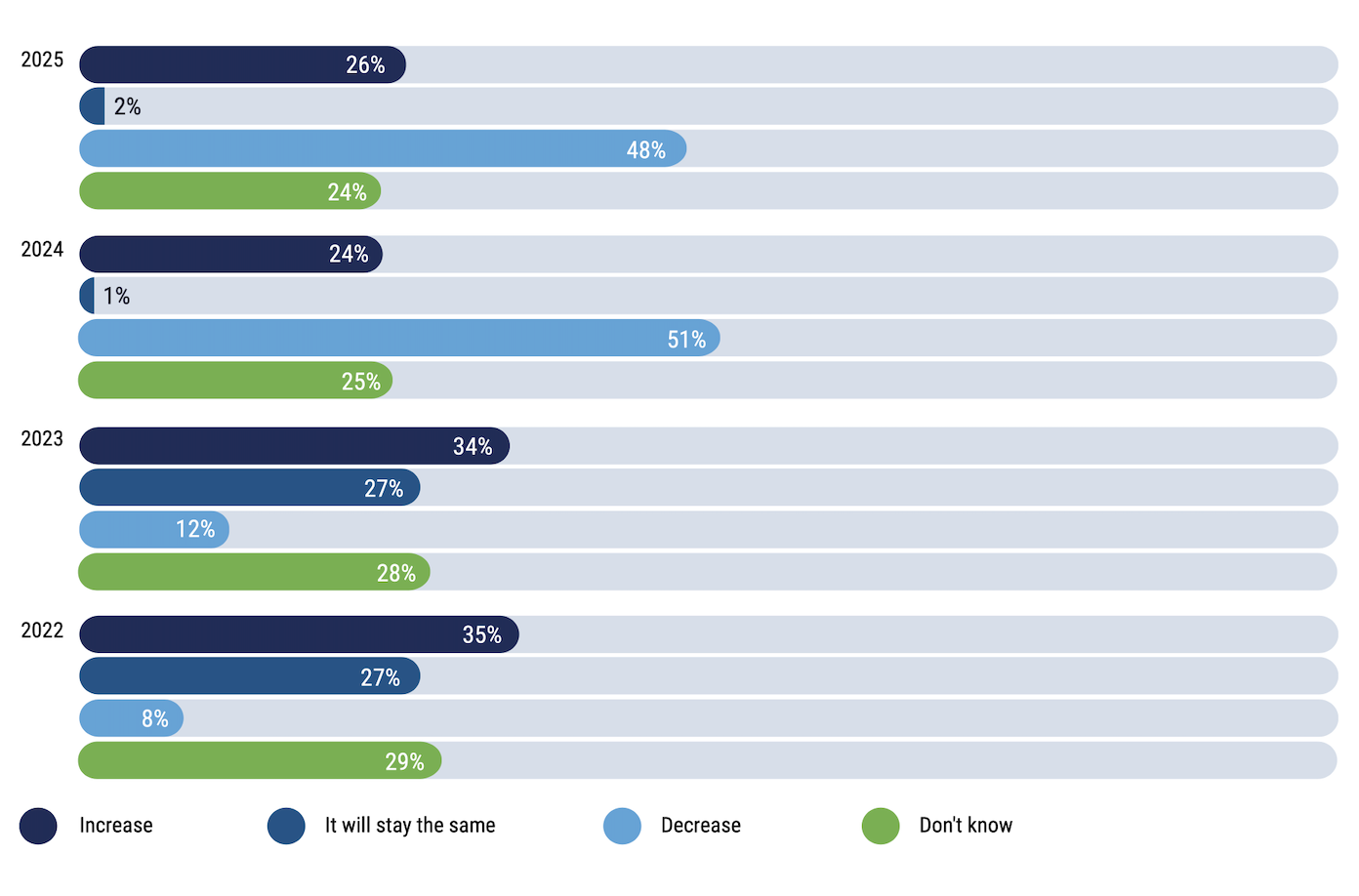
Source: ISACA’s 2025 State of Privacy
In 2022 and 2023, respondents expected budget increases for privacy, but in 2024 and anticipating 2025, expectations are that the money earmarked for data privacy will decrease. Kazi admitted that this surprised the researchers at ISACA, especially the fact that so many of the 2024 respondents (51%) expected a decrease. In the past, it was closer to 12%.
What concerns Kazi is that the fears of the budget decrease were not unfounded. In response, ISACA added a new question to the survey this year, asking for details about the respondents’ privacy budget in the last 12 months. The reality didn’t match the prediction, as only 10% said their budget actually dropped. But that could be a short-term reality.
[Read also: A guide to cybersecurity budgets in 2025]
The ISACA cybersecurity study did not find similar results in the budget question. “This leads me to believe that some enterprise teams who are already dealing with resource issues, security staffing could potentially be tasked with privacy-related responsibilities,” Kazi said. “That companies see building a privacy program as more resource-intensive than maintaining it. And once they see they are meeting compliance, they can make cuts.”
3. Data privacy compliance – expert tips and tools make a difference
Confidence in Ensuring Data Privacy and Achieving Compliance
How confident are you in your organization’s privacy team’s ability to ensure data privacy and achieve compliance with new privacy laws and regulations?
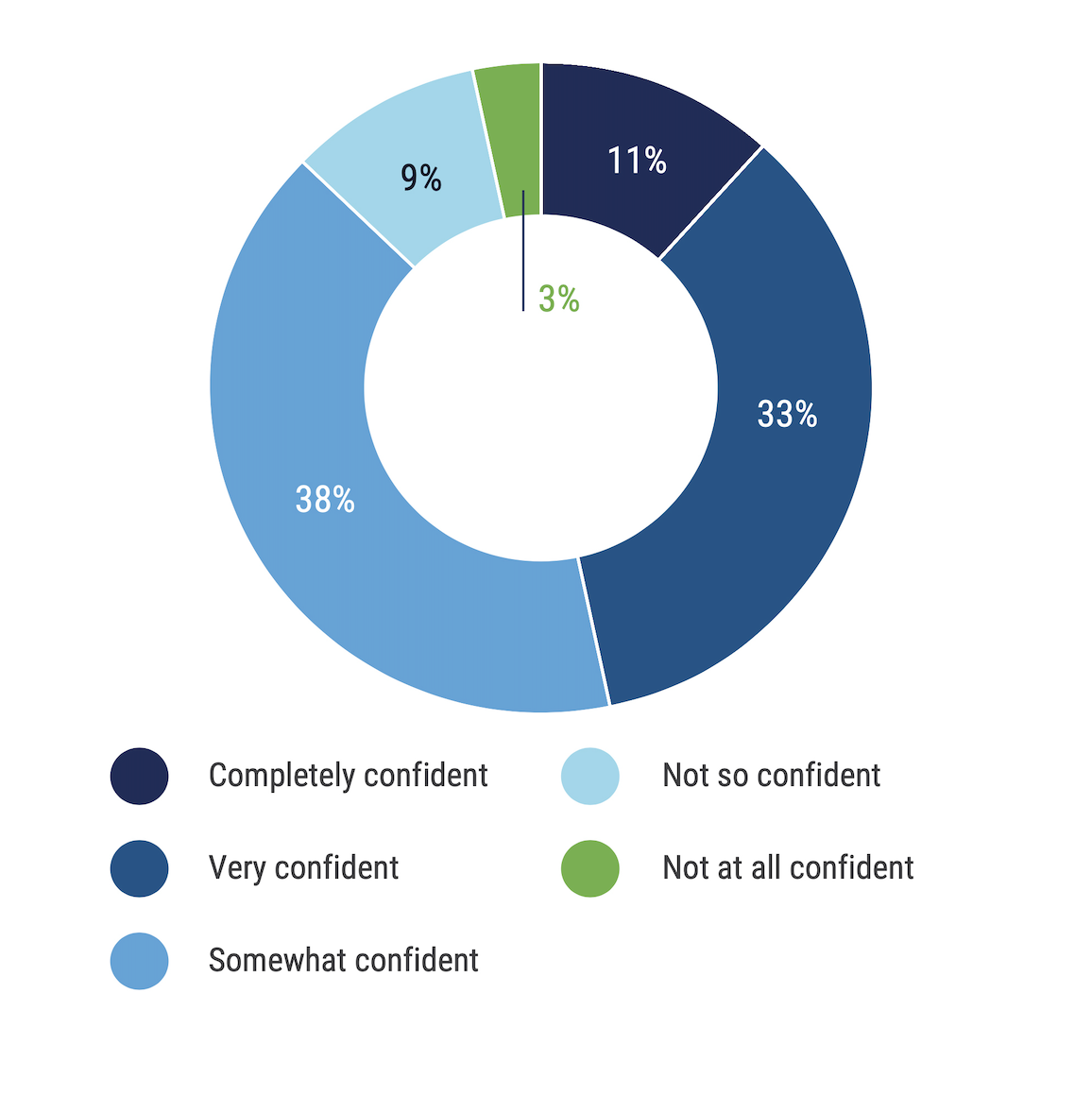
Source: ISACA’s 2025 State of Privacy
Compliance heavily influences a company’s data privacy program. If that wasn’t clear from Kazi’s comments, 82% of respondents use a compliance framework to build their data privacy program, and most rely on the advice of legal experts to ensure the company continues to meet compliance standards.
Having a regular cadence of meeting with legal and compliance professionals who are more plugged in to what’s happening as far as enforcement goes is really critical to being compliant.
“Meeting with legal and compliance teams is really critical because when a law or regulation has come out, there will be new enforcement actions that happen every single year,” said Kazi. “Having a regular cadence of meeting with legal and compliance professionals who are more plugged in to what’s happening as far as enforcement goes is really critical to being compliant.”
However, Kazi stated that organizations should also take advantage of the tools available to help with data management because they can help keep the company compliant. “I really think spending some money on good data management practices is going to give you a really good ROI.”
4. Using AI for data privacy
Plans to Use AI
What are your organization’s plans to use AI (bots or machine learning) to perform any privacy-related tasks?
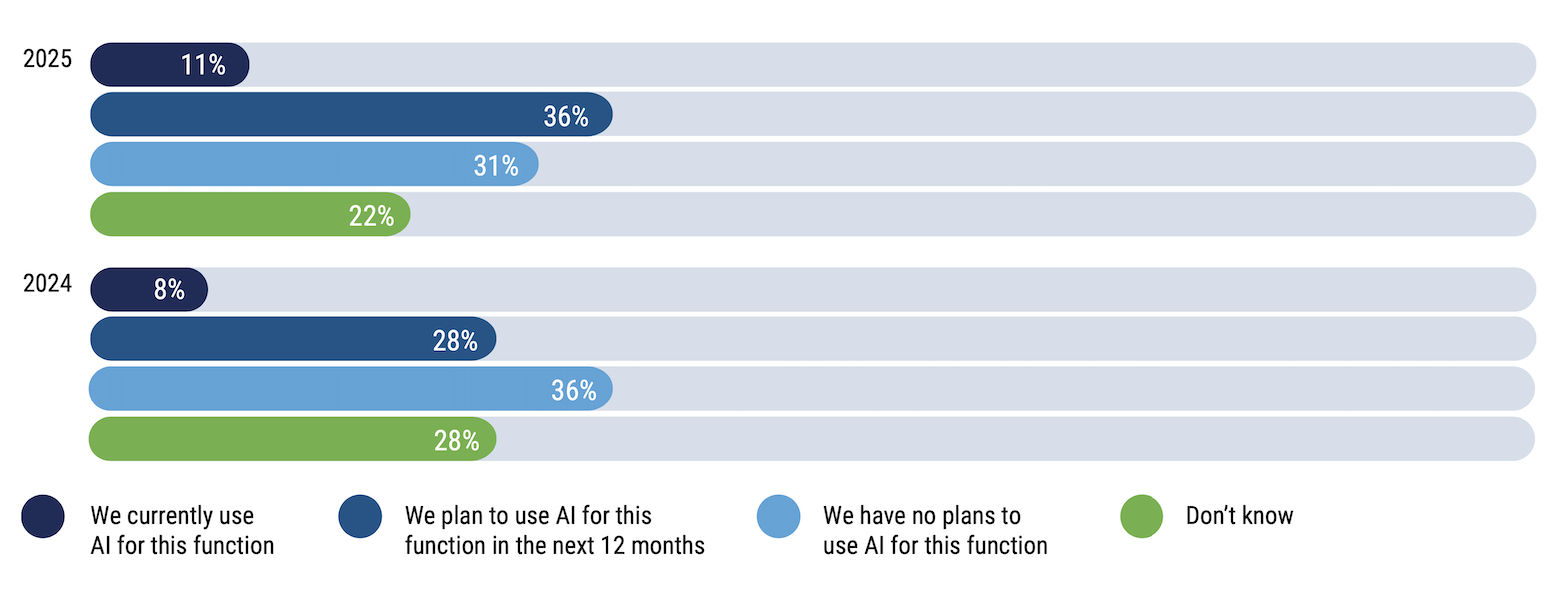
Source: ISACA’s 2025 State of Privacy
It’s impossible to talk about anything today without looking at the impact of AI. Privacy professionals are increasingly interested in using AI, not necessarily generative AI, but AI/ML, now that machine learning is increasingly being used in cybersecurity and data management and monitoring tools.
As the use of generative AI becomes more popular across organizations, Kazi thinks it will create a serious challenge for privacy professionals.
[Read also: Racing to deploy GenAI? Security starts with good governance]
“Organizations are rushing to adopt this new technology without doing privacy-impact assessments, privacy risk assessments,” Kazi said. “Privacy professionals are saying, OK, how can we make the use of this technology align with our other privacy goals and objectives. I think eventually a lot of AI governance and AI ethics tasks are going to fall to privacy professionals.”
5. Privacy by design – it’s a matter of ethics
Privacy by Design Frequency
How often does your enterprise practice privacy by design?
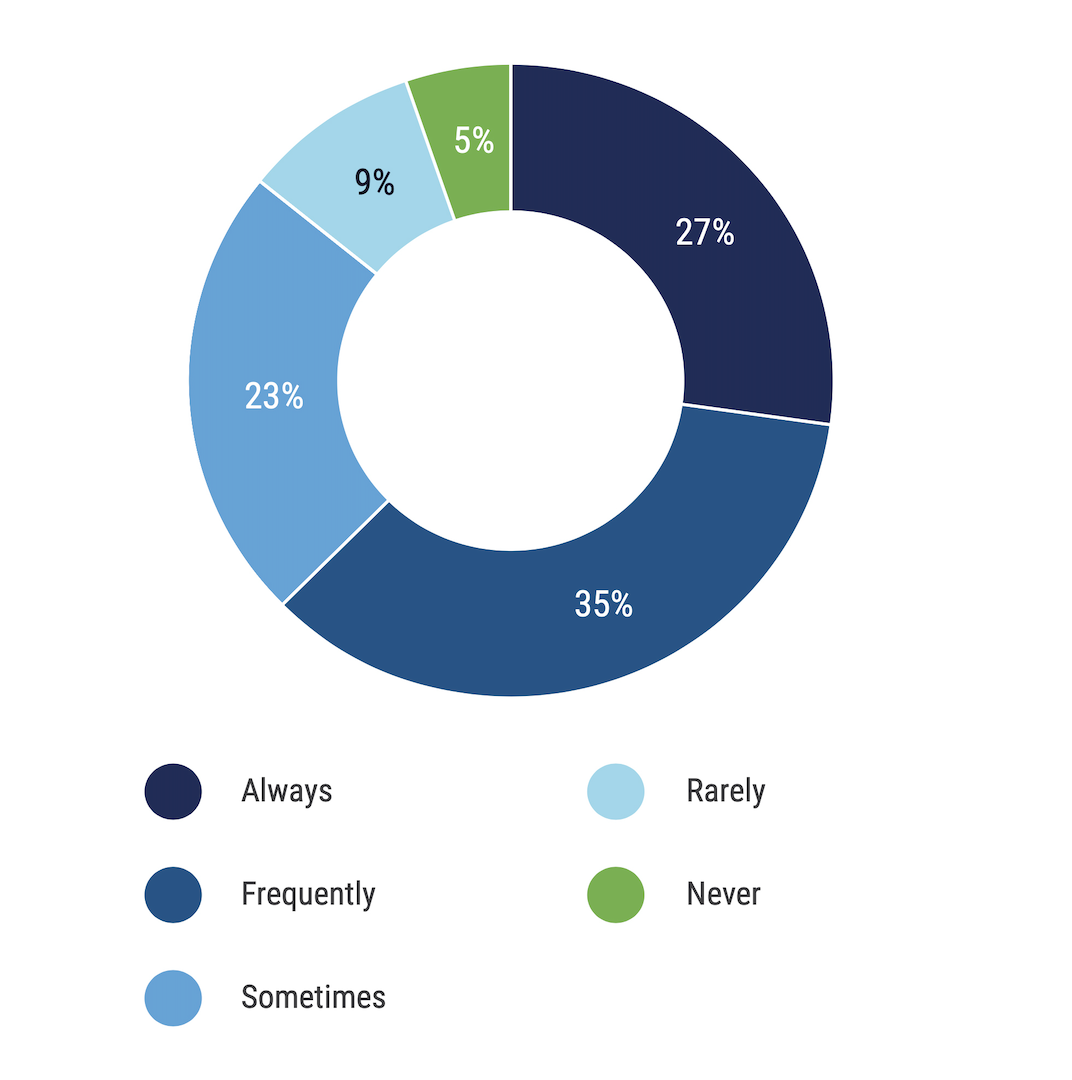
Source: ISACA’s 2025 State of Privacy
ISACA defines privacy by design as “the integration of privacy into the entire engineering process [and] is critical to ensuring that new products and services can support privacy objectives.” Two-thirds of the respondents said they use privacy by design when building new applications. And they are certainly wise to do so, given new regulatory frameworks like the EU’s AI Act, which promotes a privacy-by-design approach.
“I think a lot of our survey respondents understand that privacy by design is important,” said Kazi. “However, it can be kind of resource-intensive because it means privacy professionals need to be involved with development projects from the beginning. I think it’s totally understandable that some enterprises just say they cannot do privacy by design in every single project, so they need to prioritize.”
Budgets and compliance are all necessary to build a good data privacy program, but Kazi added one more thing that she wants people to take away from the report—why ethics around data privacy matter so much.
“Laws and regulations move so much slower than technology,” Kazi said. This means that the people who build technology need to start prioritizing ethics across data in order to protect the privacy of consumers.








