‘Tis the Season for a New Phishing Scam: Cyber Threat Intelligence Roundup
Organizations prioritize third-party risk management and gauge their own third-party security postures, Chinese hackers use Google Drive to drop malware, and a new phishing kit targets US shoppers this holiday season
First up in this week’s report is a look at a study from the Forrester research firm, exposing how prepared organizations are to face the growing supply chain risk. This is followed by a detailed exploration of a recent cyberespionage campaign attributed to China’s Earth Preta APT (aka Mustang Panda), in which the threat actors were observed delivering custom malware stored in Google Drive and Dropbox accounts to government, research, and academic organizations located primarily in Asia. Also included is a timely look at a new and highly sophisticated phishing kit that’s convincingly mimicking several large retail brands ahead of the busy holiday shopping season.
1. Despite orgs acknowledging the supply chain threat, experts suggest third-party risk management efforts aren’t up to snuff
Forrester reports via a survey-based study that, despite calls from industry experts to shore up and streamline supply chains in the wake of the COVID-19 pandemic, enterprises continue to increase their reliance upon third-party services.
Whether the driving force behind this paradigm is the desire of organizations to optimize productivity, remain competitive, or simply increase business agility, the bottom line is that increased reliance upon third parties is often accompanied by a commensurate level of cyber risk — particularly when an organization lacks a mature third-party risk management program.
While respondents appreciated the business benefits associated with third-party products and services, they haven’t always appreciated the risks associated with third parties. These same respondents conceded that there remains a considerable amount of work to be done to advance their third-party risk management programs to a sufficient level of maturity.
Experts seem to agree that an acceptable degree of program maturity is the result of a well-balanced combination of technical sophistication, agility, and robustness.
Key findings from Forrester’s survey
- Better decision-making through data is a high business priority for 72% of respondents.
- 71% said embracing digital business processes was a high priority.
- Improving organizational response to business and market changes was a high priority for 69% of respondents.
- In the year leading up to the survey, 40% of respondents estimated that the risk levels associated with their supply chains significantly increased, with 38% of those respondents blaming higher risk levels on an increased reliance on third parties.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“Forrester’s survey results speak for themselves. One doesn’t need to look far to find a truckload of examples of high-profile compromises that were ultimately either traced back to the exploitation of a vulnerability in a contractor’s system, determined to be the result of a supply chain compromise of a third-party vendor or linked in some way to the weaponization of code packages or libraries hidden among legitimate utilities stored in repositories leveraged daily by developers. As an example, consider the recent discovery of dozens of PyPI packages delivering W4SP info-stealing malware.”
2. Chinese hackers use Google Drive to drop malware on private networks
A recent Trend Micro report details a large-scale spear-phishing campaign in which state-backed Chinese hackers were observed delivering custom malware – stored in Google Drive or Dropbox accounts – to government, research, and academic organizations worldwide for purposes of espionage.
The attacks, which reportedly took place between March and October 2022, have been linked to the cyberespionage group tracked as Earth Preta by Trend Micro — more commonly known as Mustang Panda (aka Bronze President, or TA416). The threat actor has been targeting entities all over the world since at least 2012, including government organizations, think tanks, NGOs, and Catholic organizations at the Vatican.
Earth Preta, like many China-nexus APTs, is a cyberespionage group known to develop its own custom malware and deploy it in combination with existing tools such as PlugX and Cobalt Strike. Earth Preta has gained a reputation for its continuous efforts to update of its arsenal, and the group’s recent activity seems to support that assessment.
Following initial infection, the sensitive documents exfiltrated by Earth Preta from target networks may be leveraged to aid in gaining initial entry during the group’s next wave of intrusions. Such methodology has the combined effect of significantly broadening the scope of Earth Preta’s cyberespionage campaigns while vastly increasing the size of the attack surface in the targeted region.
Based on Earth Preta’s recent objectives, Asian countries appear to be the group’s current area of focus. Trend Micro’s researchers report that, in its most recent campaign, the threat group has primarily targeted organizations in Australia, Japan, Taiwan, Myanmar, and the Philippines.
This assessment aligns with Cisco Talos’ reporting, which lists the Taiwanese government, activists in Hong Kong, NGOs in Mongolia and Tibet, Myanmar and even Afghan and Indian telecommunication firms as targets featuring in Earth Preta’s impressive victimology.
Earth Preta campaign details
Trend Micro reports that during the widespread spear-phishing campaign referenced above, Earth Preta was observed abusing fake Google accounts to distribute the malware via spear-phishing emails, initially stored in an archive file (with extensions like .rar,.zip, and .jar) and distributed through Google Drive links. The hackers primarily focused their efforts on government and legal organizations, which comprise 84% of the campaign’s victimology to date.
Earth Preta was also observed utilizing a range of techniques in support of detection evasion and anti-analysis, such as code obfuscation and the use of custom exception handlers. These techniques were leveraged in combination with embedded links pointing to Google Drive or Dropbox folders. Both are legitimate, trusted platforms used by a vast number of private and public organizations in support of daily operations, and their good reputations help achieve the attackers’ intended effect: making malicious traffic appear innocuous.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“Earth Preta is well-resourced, with access to the shared tools preferred by Beijing’s legions of state-backed hackers and the ability and manpower to continuously upgrade its arsenal and create its own bespoke malware. The group’s anti-analysis and defense evasion techniques are indicative of a strong focus on operational security (OPSEC). To some degree, the same can be said for Earth Preta’s use of at least three different malware delivery vectors in a single spear-phishing campaign. Proceed with caution.”
3. Phishing kit impersonates well-known brands to target US shoppers during holidays
Recent security research from Akamai uncovered a new and highly sophisticated phishing kit that is mimicking several large, well-known retail brands ahead of the holiday season.
The kit uses a mixture of social engineering, multiple detection evasion techniques, and capabilities enabling attackers to bypass access control security measures.
Campaign overview
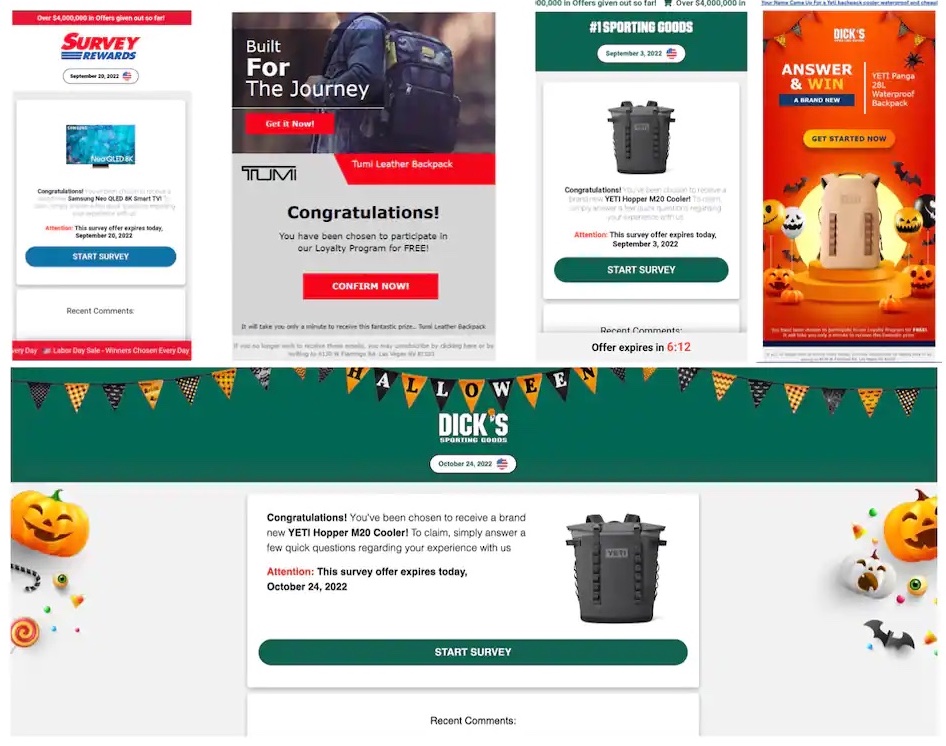
Akamai uncovered an ongoing phishing campaign that occurred from mid-September 2022 through October 2022 that preyed on online shoppers looking to take advantage of holiday specials. This campaign enticed victims with the chance to win a prize, requesting credit card details to “cover the cost of shipment.”
The timing of the campaign – designed to coincide with the common promotional sales e-retailers push around Labor Day and Halloween – serves to increase its sense of legitimacy and capitalizes upon the commercial fervor that tends to grip Americans this time of year. Or, put less cynically, the campaign takes advantage of users by playing into the holiday spirit and mimicking legitimate retail marketing ploys. The phishing emails are sophisticated when it comes to their appropriation of authentic branding, as you can see in the sample below.
Social engineering techniques
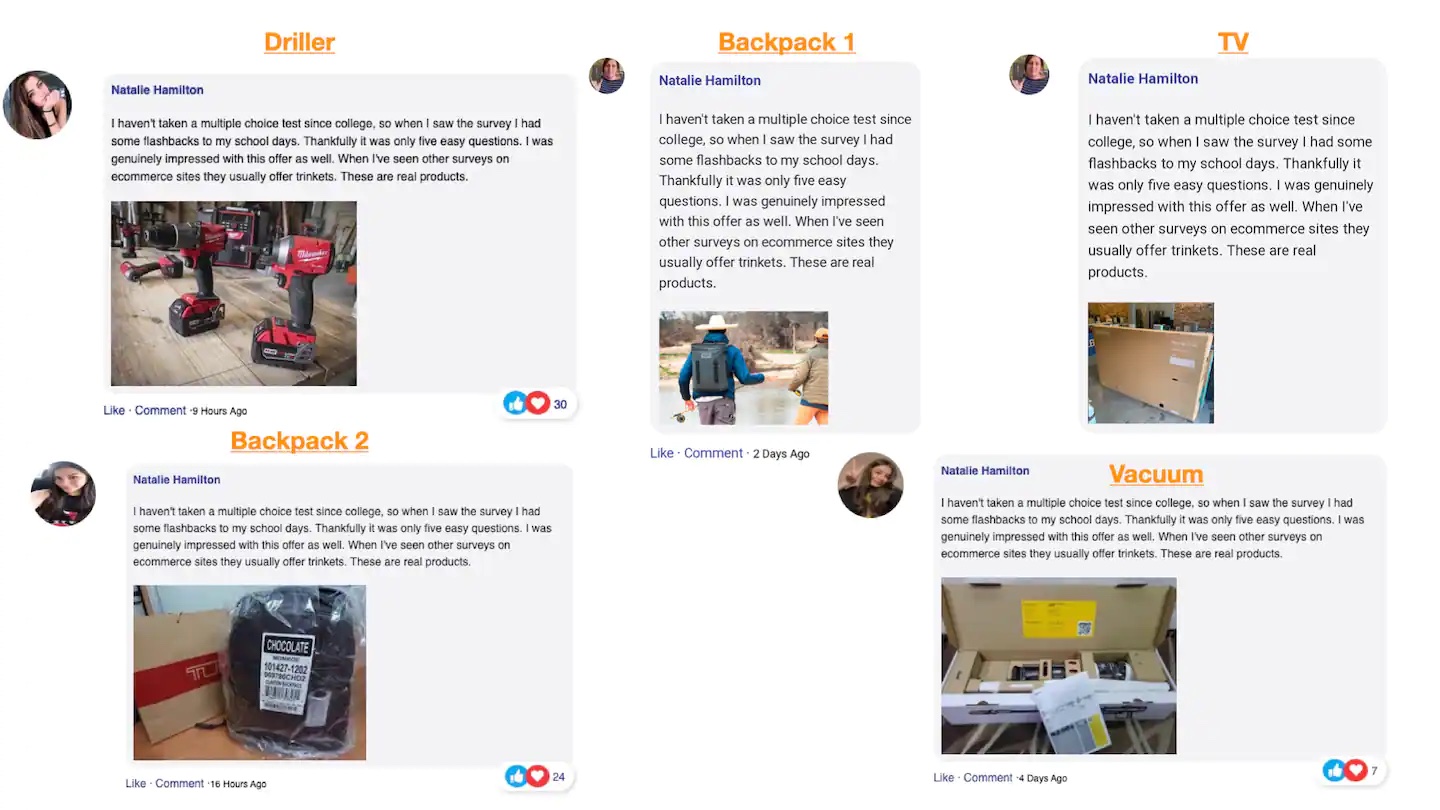
The phishing emails used in this campaign mimic a wide range of brands. One similarity between many of the emails was a fake user named Natalie Hamilton. This user was leveraged across multiple scams leaving prize review comments to make the prize seem genuine. This technique is used to establish trust with the user and some examples of it can be seen below.
Campaign infrastructure
Akamai was able to identify a nested chain of redirections, starting with the initial link delivered to victims in the phishing email. This link eventually redirects victims to the final landing page of the scam. The use of a nested chain of redirections is what prompted Akamai’s researchers to characterize the campaign as “highly sophisticated.”
Detection evasion techniques
This campaign leverages a few different techniques as it attempts to evade detection:
Abuse of URL shorteners: URL shortening services such as Bitly have become so normalized, due in large part to their ubiquitous use on social media platforms, that many consumers no longer think twice when clicking on a shortened URL. This is exactly what this phishing kit aims to take advantage of and abuse. This threat actor has created fake LinkedIn profiles to create posts pointing to the malicious destination, assigning them the shortened URLs featured in the initial phishing emails.
Exploiting legitimate web services’ reputation: The threat actors use a legitimate service provider to host their malicious redirection functionality. By using services like Google cloud storage, AWS hosting services, and Azure blob storage, the threat actor is taking advantage of the good faith with which users view the reputations of these services. This increases the chances of bypassing anti-phishing mechanisms that may be in place.
URL fragment identifier redirection: The URL fragment identifier is a hash mark of the URI link that points a browser to a specific spot on a page or website. This technique is commonly used in a table of contents to create a better user experience. In the context of a phishing campaign, however, the hash may be ignored or overlooked when scanned by security products. In this campaign, the original link sent to victims contains a hash mark followed by a token. The token is later used by JavaScript to reconstruct a URI that the victim will be redirected to. The usage of tokens also enables the adversary to track victims and look for statistics on potential victims’ engagement.
Randomly generated URLs: A notable part of this campaign is its attempts to filter out unwanted visitors to its specially designed redirects, landing pages, and phishing sites. To do so it generates a random URL that is tied to a specific user, and included as part of the chain of redirects. After landing on the phishing website, each allocated URL can only be used by the specific user, leading to lower detection rates.
Power of the CDN: As is the case with the abused web hosting services, the landing page of the scam uses some of the services being offered by a CDN vendor, including domain registration. The threat actor utilizes quick and easy domain registration to spin up an instance and then rotates the phishing domain name without needing to take down the infrastructure. It also rotates the IP addresses associated with the CDN, eliminating the possibility of blocking the activity based on the IP address.
Geo-targeting: The landing websites appear to change based on the victim’s geographic location, with some geographic locations not being prohibited at all. The campaign tracked by Akamai was primarily targeting victims located in the United States, with 89% of the observed victims being in either the United States or Canada. The same initial phishing link leads to various websites with geographic customization further emphasizing the efficacy and sophistication of the campaign.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“The campaign observed by Akamai aligns with historical trends of threat actors taking extra advantage of consumers during the holiday season. This campaign is likely just the beginning of this type of activity as we move into the holiday season. This story is a reminder for everyone to stay on their toes this holiday season. Be extra cautious when opening holiday promotional emails, e-cards, online order confirmations, shipment tracking emails, etc. Remain vigilant, and keep an eye out for any unexpected/unsolicited communications from retailers.”
For further reading, catch up on our recent cyber threat intelligence roundups.