Featured stories
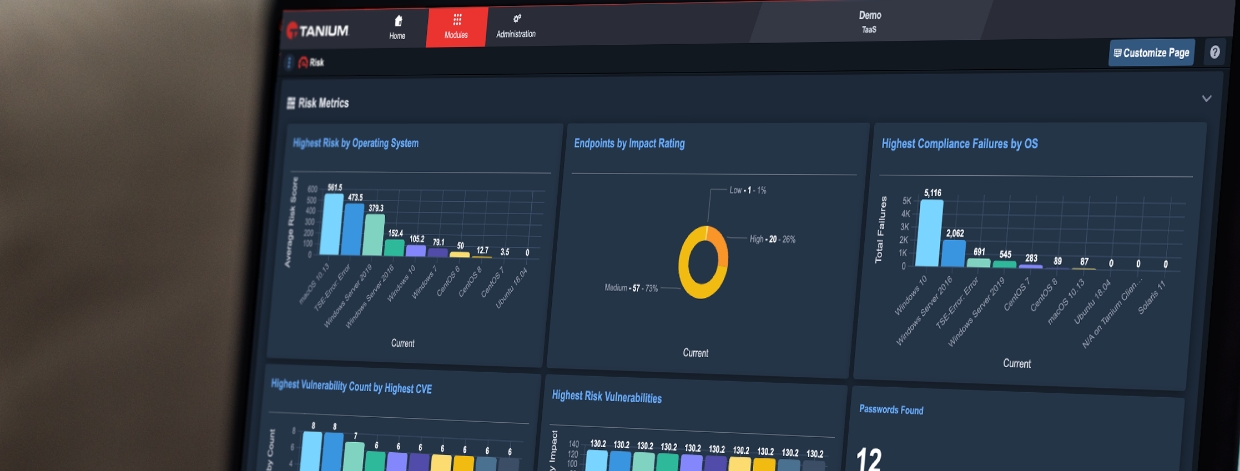
New Tanium Security Operations for ServiceNow Gives Organizations a Powerful Cybersecurity Solution
This new solution empowers teams to identify, correlate, prioritize, and remediate risk of endpoint vulnerabilities and incidents in real time.
Partner Spotlight