7 Ways Tanium Can Protect Your Organization From Evolving Cyberthreats and Data Breaches
Traditional incident response tools can’t cope with modern attacks or deliver a meaningful improvement to endpoint security
Fifteen years ago, most organizations were worried about very formulaic cyberattacks designed to hit every enterprise or every computer out there. Attackers were in it for the glory. They were trying to get publicity and cause a lot of disruption.
But times have changed. Today we’re looking at very targeted and sophisticated attacks, many of them by nation-states or professionally driven.
Attackers are going after data they can sell or use to cripple organizations and governments.
In this blog, we’ll explain why traditional incident response tools can’t cope with these attacks. And we’ll describe how Tanium can empower you to manage complex, emerging threats with the visibility and control required to detect, respond to, and remediate threats — before they cause material harm.
“One of the biggest security challenges from a technology perspective is the old adage that ‘the perimeter is dead’,” says Kris McConkey, Cyber Threat Operations Lead Partner, PwC.
Most incident response tools fail to do the job
How big is cybercrime? Well, it’s projected to inflict damages of $6 trillion USD globally in 2021. Measured as an economy, that would put it third behind only the U.S. and China.
Organizations have attempted to defend themselves against this onslaught of new and complex threats by adopting multiple new security tools. Yet it’s become very apparent that these tools are too rigid and narrowly focused to be effective — in either detection or response.
“In working with clients on hunt engagements, Booz Allen has found an average dwell time — that is, the time an advanced adversary lies undetected in a victim’s network — of 200-250 days before discovery.”
That squares with Verizon’s 2019 Data Breach Investigation Report, which found only 3 percent of organizations find a breach when it occurs.
Traditional incident response tools usually fail to deliver a meaningful improvement to endpoint security because their approach is flawed. And these flaws include:
- Slow, siloed, and limited detection and investigation capabilities
Most tools offer minimal context for security investigations and rely on narrow windows of historical telemetry — maxing out at 7-30 days — forcing teams to analyze threats using incomplete, outdated, inaccurate data.
- Fragmented, narrowly focused, and siloed remediation capabilities
Most are point solutions focused on limited use cases, requiring organizations to continuously expand their toolset to defend against individual threats, without improving their security posture as a whole.
- Poor results against modern threats in modern environments
Most have not adapted their approach to handle threats that do not follow simple, predictable patterns, and lack the flexibility required to combat dynamic threats that target modern, distributed endpoint environments.
Not only do these tools not provide the protection that organizations need, but they also overload IT departments with a growing menagerie of single-use solutions that are difficult to manage. Security teams are left in a reactive position, flooded with alerts and threat data but without the ability to improve their risk posture.
Seven ways Tanium can help
Tanium’s approach to incident response provides comprehensive visibility into the endpoint environment, allowing organizations to hunt for subtle indicators of compromise that suggest novel attacks — attacks traditional tools are likely to miss. Security teams can investigate threats faster and compare historical and current data to develop a clear picture of how a threat emerged and developed, and what objectives it’s trying to achieve. Tanium combines these detection capabilities with a robust suite of remediation actions, all within a single platform.
With Tanium, your IT team can:
- Reduce mean time to investigate and remediate threats
Rapidly identify, investigate and map the extent of each threat and determine the correct response in real time. Eliminate threats from your environment faster, preventing their objectives and containing their damage. Assess the extent of — and contain — a breach with up to one year of historical data.
- Lower risk in your endpoint environment
Shrink your attack surface and improve the overall risk posture of your endpoint environment. Detect and respond to known and unknown threats as they emerge. Create a healthier endpoint environment hardened against future attacks.
- Integrate with a wide range of threat intelligence feeds
Tanium can adapt to the nuances of your endpoint environment. You can tailor details from the threat intelligence you deploy to the granular rules used by both endpoint and SIEM solutions to determine what is a true incident. Take advantage of Tanium’s connector with OpenCTI (Open Cyber Threat Intelligence), an open-source platform that allows organizations to manage cyber threat intelligence knowledge.
- Improve recovery time
Perform remediation activities across your endpoint environment in hours —not weeks or even months.
- Increase efficiency at scale
Give your security teams a higher-leverage solution and automate as many core incident response actions as possible. Rapidly pivot investigations from a single endpoint to the entire environment seamlessly.
- Streamline your IT stack
Eliminate point solutions and consolidate multiple incident response functions within a single, flexible, and extensible agent.
- Combine endpoint security and operations workflows
Perform most detection, response, and remediation actions within a single console under the same platform.
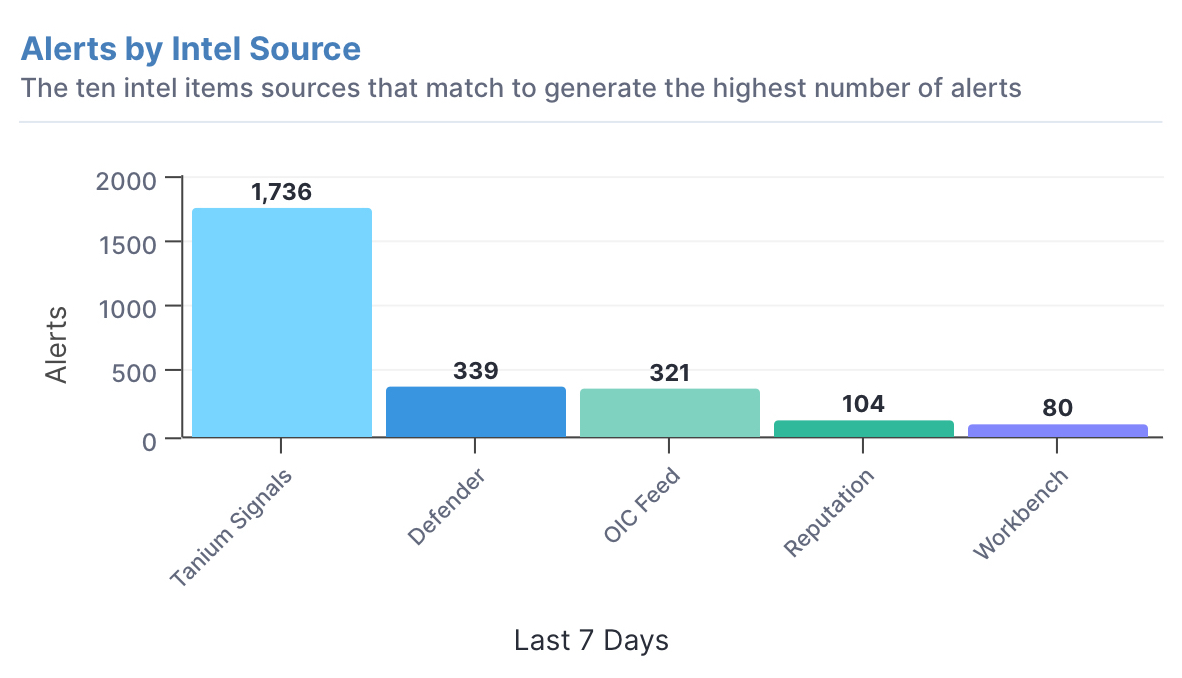
Get alerts in real time with Tanium Signals
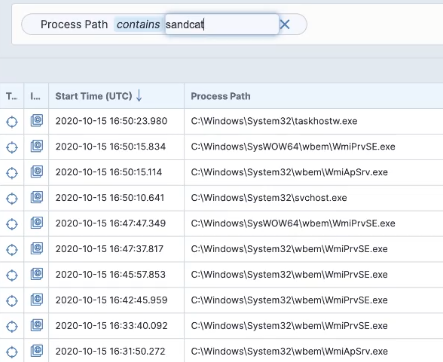
Tanium allows organizations to scope and remediate at scale with enterprise-wide questions
Four simple steps to enhanced security and better incident response
Tanium delivers incident response through unified endpoint security that increases in effectiveness the longer it’s used. Many of our customers follow a four-step process that gives them the immediate ability to detect and respond to threats in their environment, while hardening their endpoints and improving their overall risk posture.
Here’s how to do it in just four steps:
- Create real-time visibility by creating a more comprehensive picture of the endpoint environment and establishing continuous monitoring for threats. Tanium usually finds 10-20 percent more endpoints than our customers knew they had.
- Detect and contain threats by allowing ad hoc investigations or by automatically alerting security personnel when patterns are found. Tanium can quickly search across the endpoint environment for known attack patterns or suspicious behavior.
- Remediate threats and harden the environment by applying the appropriate controls across compromised or at-risk endpoints across the enterprise. Tanium can perform common remediation actions — such as applying patches, managing firewalls, or enforcing configurations.
- Establish continuous monitoring to help ensure each threat they remediate does not easily reoccur or spread within their environment. Tanium can take findings from incidents and leverage them through native OS security controls at scale, to continuously harden and protect endpoints.
Tanium Incident Response workflows and solutions are part of a broad unified endpoint management and security platform
The Tanium Platform provides a modular suite of solutions that can be adopted individually or in its entirety — to either fill gaps within an organization’s existing endpoint capabilities, or to give them comprehensive endpoint management solutions through a single platform.
Role-based access allows users from multiple groups to safely use the solution simultaneously and delivers benefits throughout your entire organization. Tanium reduces the chances of experiencing a breach, decreases the damage suffered when a breach occurs, and improves your overall risk posture.
IT operations team
Discover and close vulnerabilities in your environment, reducing the volume of breaches by raising the barrier to entry for malicious actors.
Executive team
Reduce point solutions and consolidate most endpoint security and management actions within a single, unified, lightweight platform.
Information security team
Gain a comprehensive suite of tools to detect, investigate, respond to, and remediate threats before they cause material harm.
“Anything worth stealing that sits on a computer someone will eventually steal — or be prevented from stealing,” explains Orion Hindawi, Tanium co-founder and CTO. “The question organizations must ask themselves is, ‘Do we have anything worth stealing?’ Most will answer, ‘Yes.’”
Tanium is built to address today’s challenges
Tanium can deliver fundamental, holistic and effective incident response for the most demanding and complex operational ecosystems. In most cases, our out-of-the-box solutions, modules, and workflows provide the tools our customers require to gain more complete, context-driven visibility over their IT operations.
Learn more about the Tanium Incident Response solution and sign up for a demo today.