Elementary, My Dear Watson: Sherlock Holmes’ Cybercrime Investigation
“The world is full of obvious things which nobody by any chance ever observes.” -Sherlock Holmes
All detective stories have a crime, motive, investigator, and clues. I’ve always loved detective stories because they consistently involve thinking and questioning: Why does this person behave this way? What was his motive? And what weapon was used?
When we think of Sherlock Holmes, Sir Arthur Conan Doyle’s famous detective, we think of a brilliant mind, sharp observation skills, and great deductive powers.
Investigating a crime involves many processes carried out by a variety of professionals. They might be categorized into three broad stages: at the scene of the crime, in the lab, and in the courtroom. Similarly, a cybersecurity investigation involves its own stages of detection: activities done on the endpoint, analysis of indicators of compromise, and collection of forensic evidence for legal purposes.
The police tape
You could be arrested for interfering, hindering, or opposing a police officer if you cross caution tape that has been deployed by the police. Similarly, Tanium can apply yellow crime scene tape on endpoints to stop any outbound or inbound communicating with network resources. At the same time, it allows our cybersecurity detectives to keep on working on the scene from the Tanium server while conducting the investigation.
With Tanium quarantine, you can isolate a Windows, Linux, or Mac endpoint that shows evidence of compromise or other suspicious activity.
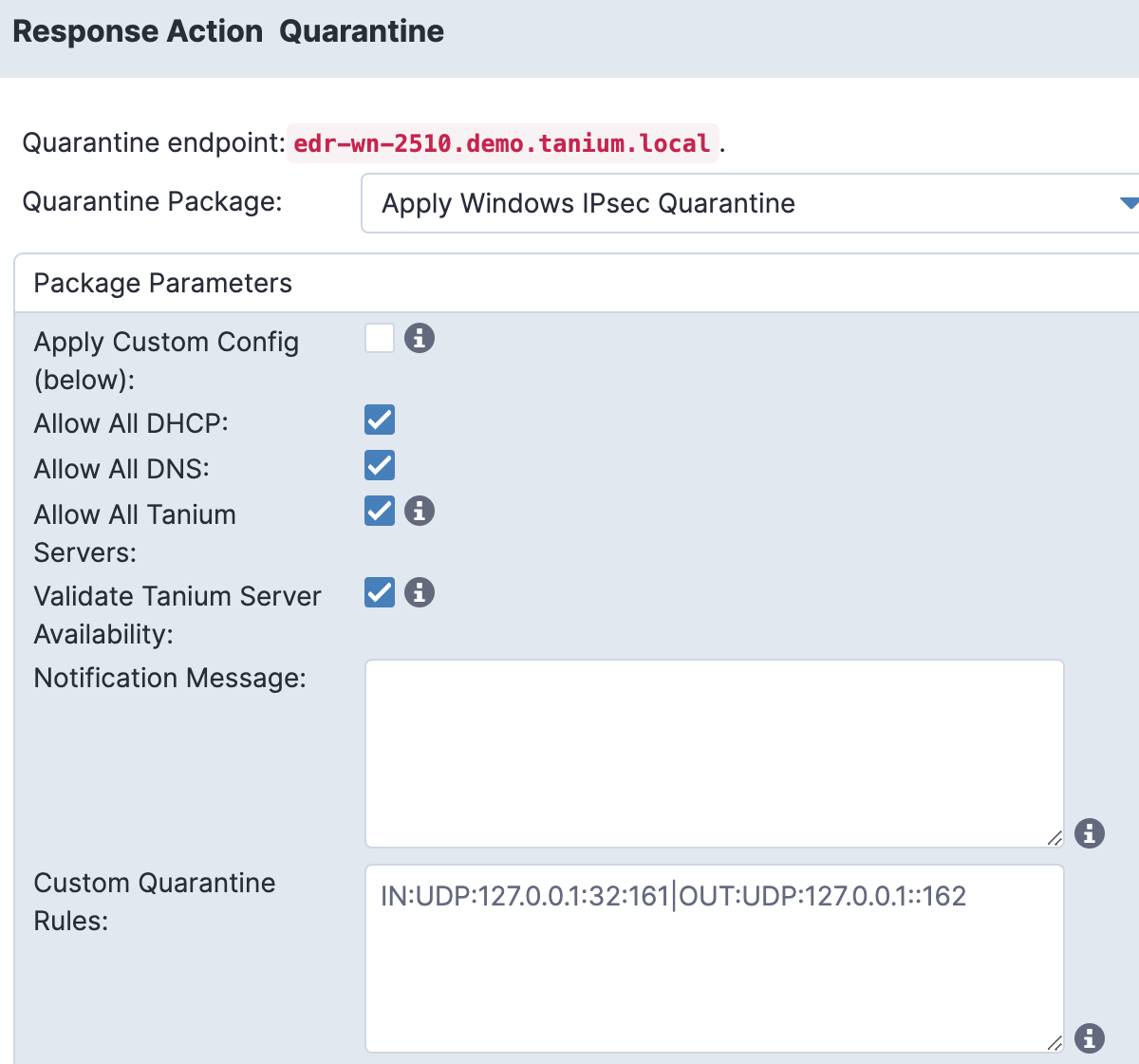
Tanium isolates an endpoint
The fingerprints
Listening to the most famous detective in the world, Sherlock Holmes, can help security analysts with their investigation.
“There is nothing like first-hand evidence.” Indicators found within the corporate environment are what you should look at first.
Indicators or indicators of compromise (IOC) are the clues in a cybersecurity detective story. They are the artifacts observed on a network or in an operating system that most likely indicate a computer intrusion. For example, MD5 of malware file, IP address or host name of C&C, delivery email address, and so on.
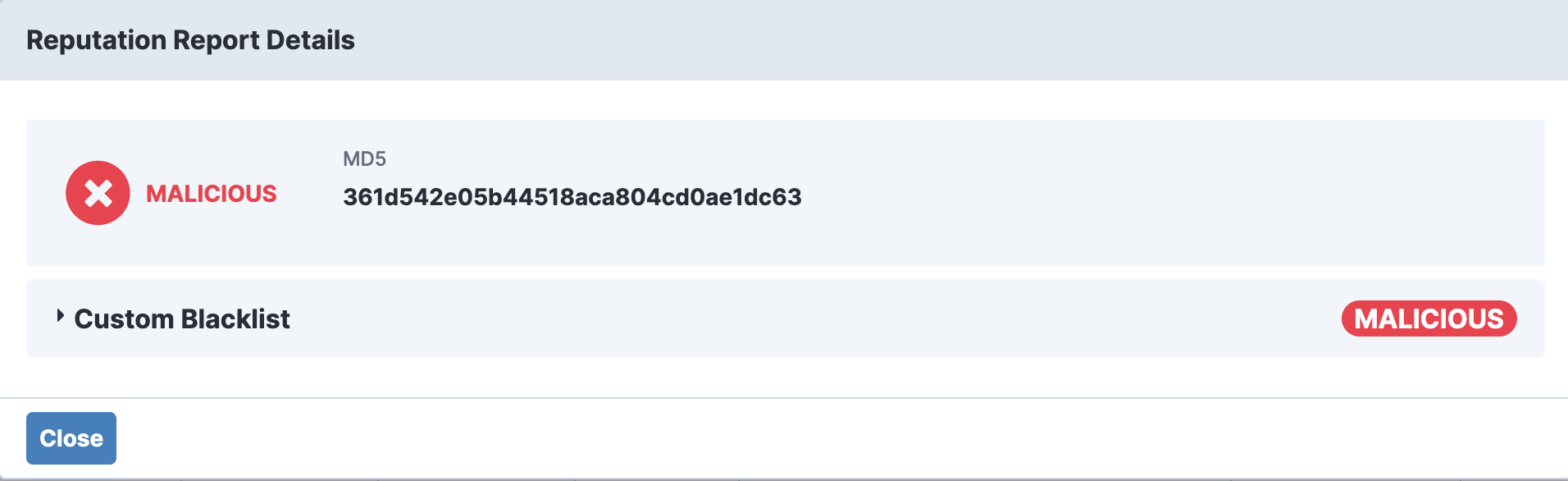
Example of a malicious hash of a malware
The weapon
A good detective will keep asking, “Is there anything here I can use to discover the adversary’s activity and which weapons or malware family were used in the attack?”
This is the weapon used to commit the offense and it is an important piece of solving the crime.
Tanium Signals can help identify weaponized files and commands using “living off the land” tools on an infected endpoint. It describes the suspicious behavior of an endpoint based on predefined rules—for example, process, network, registry, and file events for malicious behaviors and methodologies of attack. The chart below shows how malicious power shell scripts were used to enumerate domain accounts for internal reconnaissance.
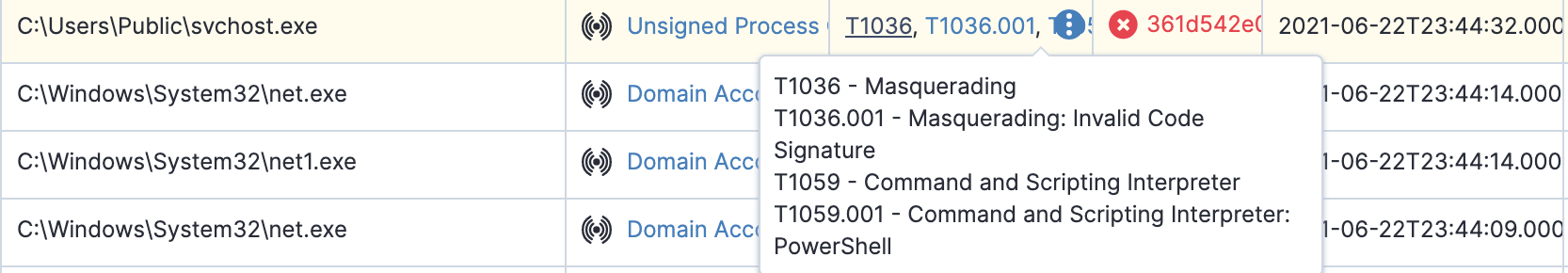
Tanium Signal can identify malicious tools and “living off the land” activities
The forensic evidence
Our modern Holmes should have forensic skills to build the comprehensive picture of the attack over time.
Digital forensics collection and analysis are critical for remediation as well as placing the proper controls to prevent future similar attacks. Tanium helps with quick and comprehensive forensics collections and storage from infected endpoints.
Tanium Threat Response can gather the forensics from an endpoint
Forensics serve as eyewitness for malware analysis and threat intelligence gathering.
Tanium can empower forensic teams to meet the demands of modern forensic analysis. Incident response lifecycle may include the following additional steps before re-imaging an endpoint.
The eyewitness interview
Just as Holmes would interview an eyewitness to a crime, Tanium process tree provides insights into the sequence of events leading to an intrusion.

A process tree visualization in Tanium Threat Response
The process tree view displays the file, network, registry, and child process activity that is initiated by a current process. This page also provides the process image path and arguments, user context, hash, and the parent command line — a tree view of network processes display, including the current process, parent, child, and peer nodes.
Cleaning up the crime scene
Crime scene cleaners (also known as bioremediation specialists and forensic cleaners) disinfect the crime scene and provide professional and compassionate services to families dealing with the crime.
Tanium’s remediation services help clean the crime scene by killing processes, stopping services, deleting files and registry entries, and more.
Remediation purge policies are used on lost or stolen endpoints by remotely wiping nonessential data or freezing the endpoint to prevent attempts to sign in.
Cyber hygiene
In addition to crime investigation, Tanium can also help prevent cybercrime. By supporting patch operating systems (Tanium Patch), updating security features on third-party applications (Tanium Deploy), and continuously looking for vulnerabilities and misconfigurations (Tanium Comply), Tanium helps keeps your neighborhood safer and less susceptible to crime.
Lessons learned
Tanium tools help with endpoint crime scene investigations. While all crime scene investigations pose their individual complexities, some situations may involve atypical locations or requirements about which law enforcement personnel and other responders should be aware.
With an interest in information security and forensics from an early age, I was drawn to the cybersecurity domain, much like Sherlock Holmes to a difficult case.
Cyberforensics has become a popular topic in security. It is important to be agile and learn quickly, particularly as it has become one of the fastest-growing and important areas of enterprise security.
Tanium gives cybersecurity investigators great tools for detection, investigating, containing, and remediating cybercrimes.
Learn more about Tanium’s endpoint security and risk solutions and request a free cyber hygiene assessment to see what’s on your network.