Tanium value metrics
Through comprehensive and real-time analytical insights about their devices, Tanium helps organizations measurably improve IT hygiene, employee productivity and operational efficiencies while reducing risk, complexity and costs.
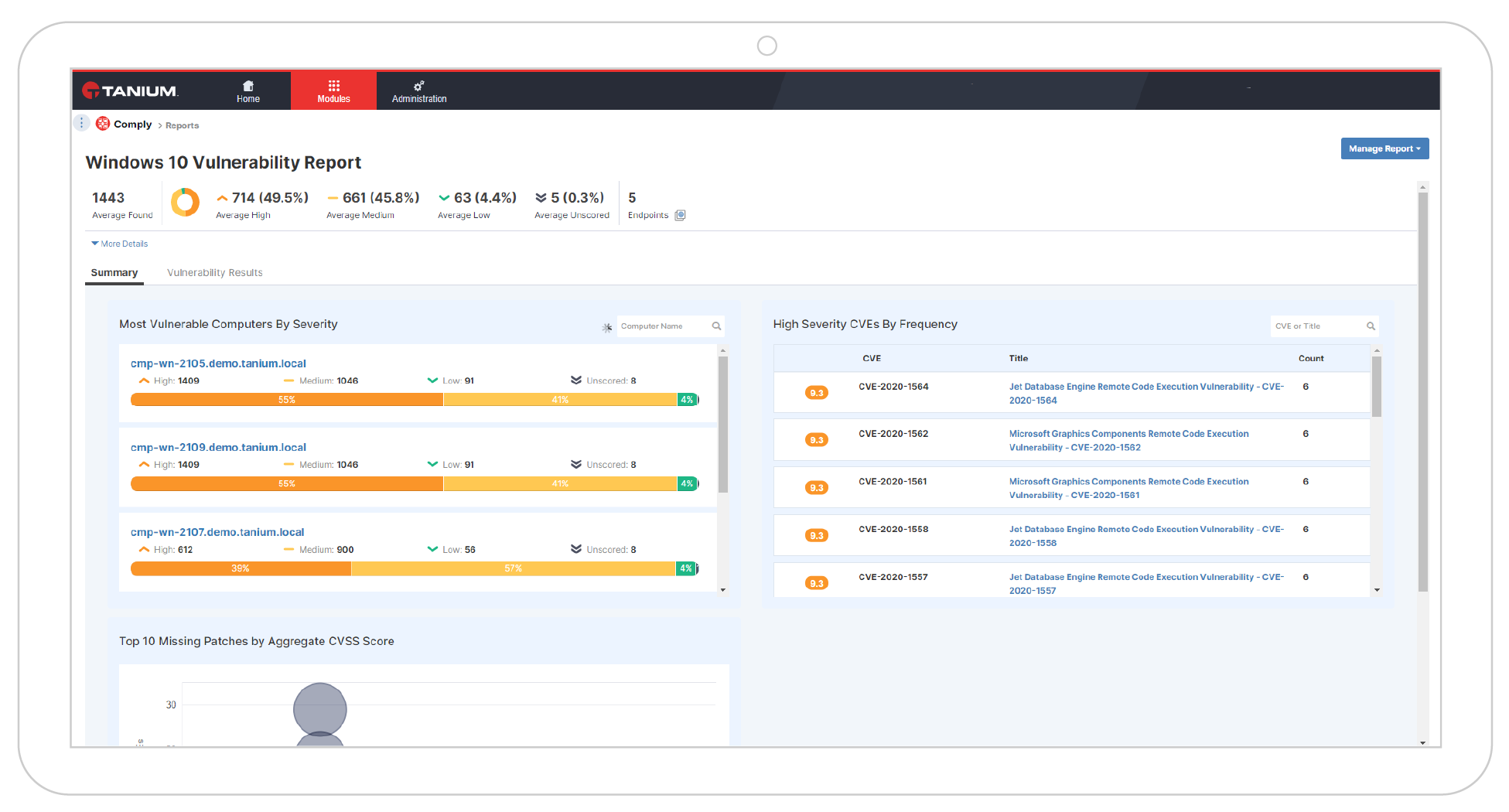
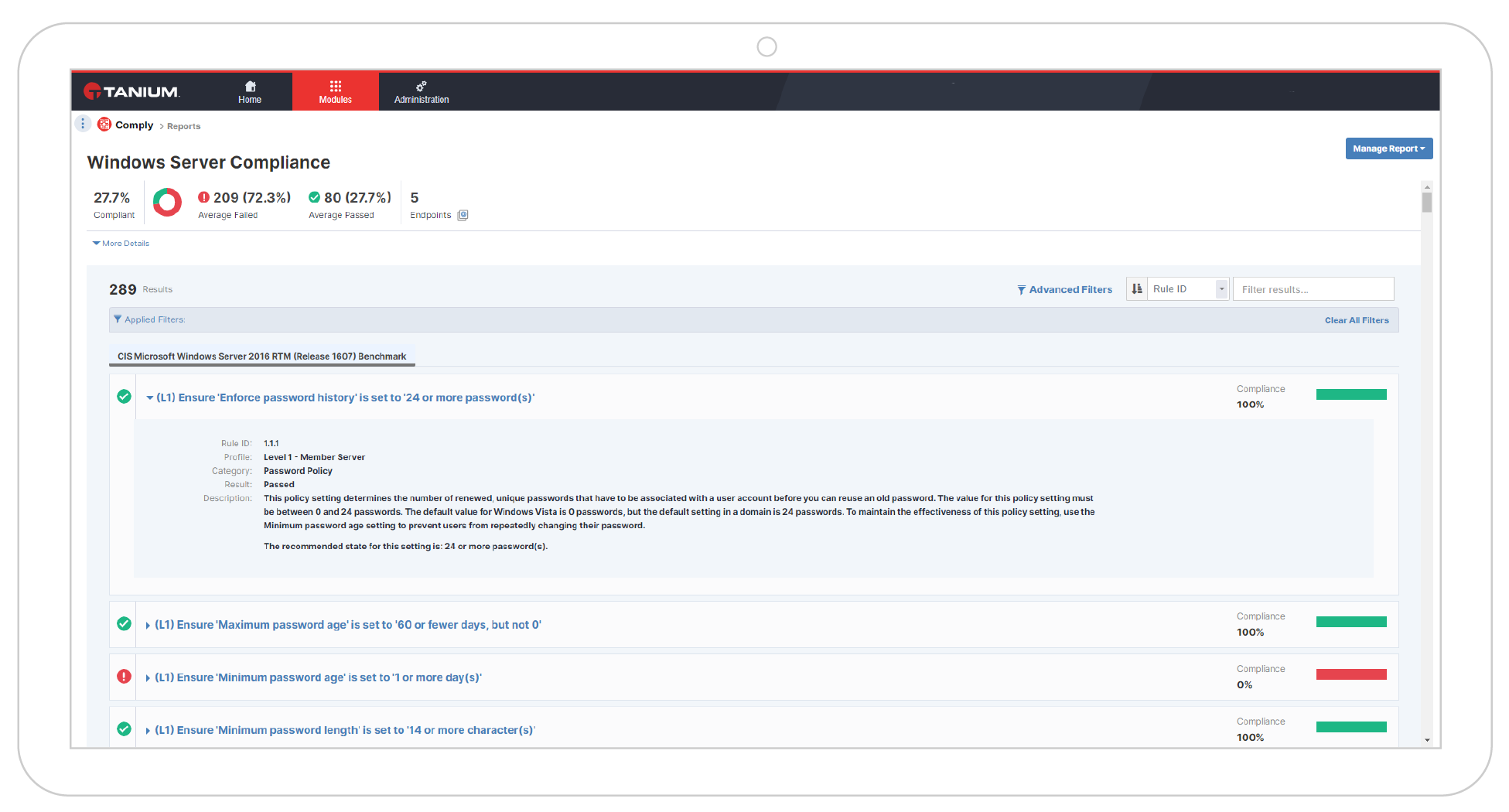
Comply coverage (% of total endpoints)
Are your endpoints compliant? The percent of total endpoints covered shows gaps in compliance assessment coverage that lead to inaccurate data and increase exposure to vulnerabilities.
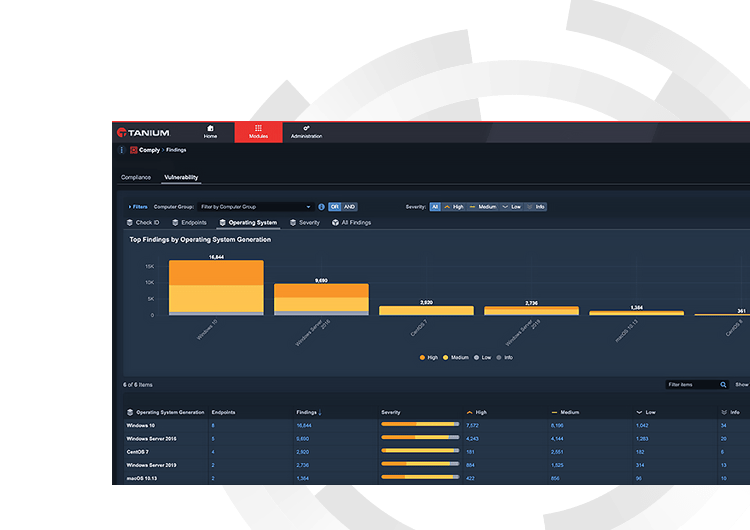
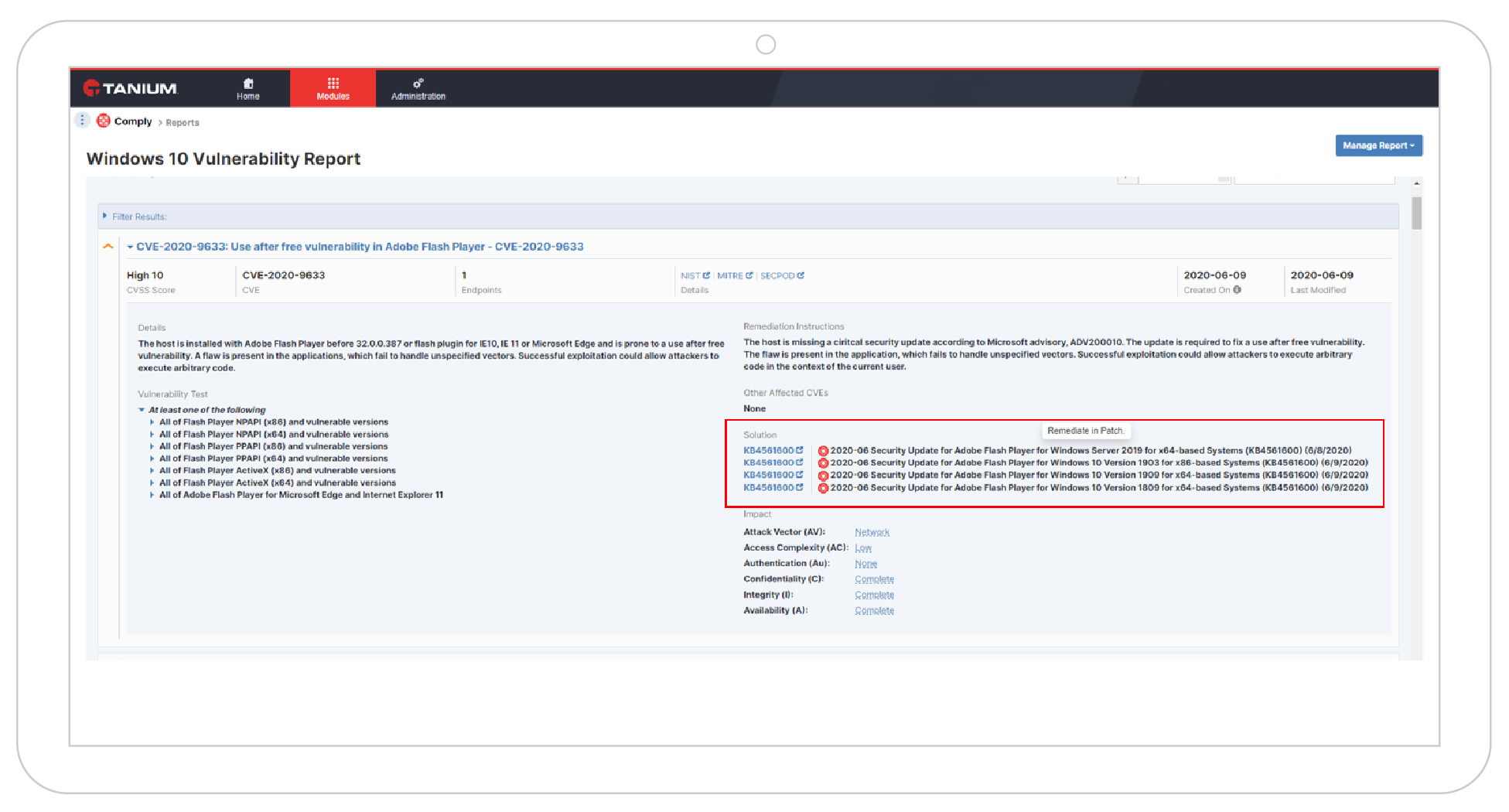
Endpoints with critical or high vulnerabilities (% of total within coverage)
How many of your endpoints have critical vulnerabilities? The percent of total endpoints with critical vulnerabilities measures the quantity of endpoints with security exposures, which put organizations at greater risk of disruption or breach.