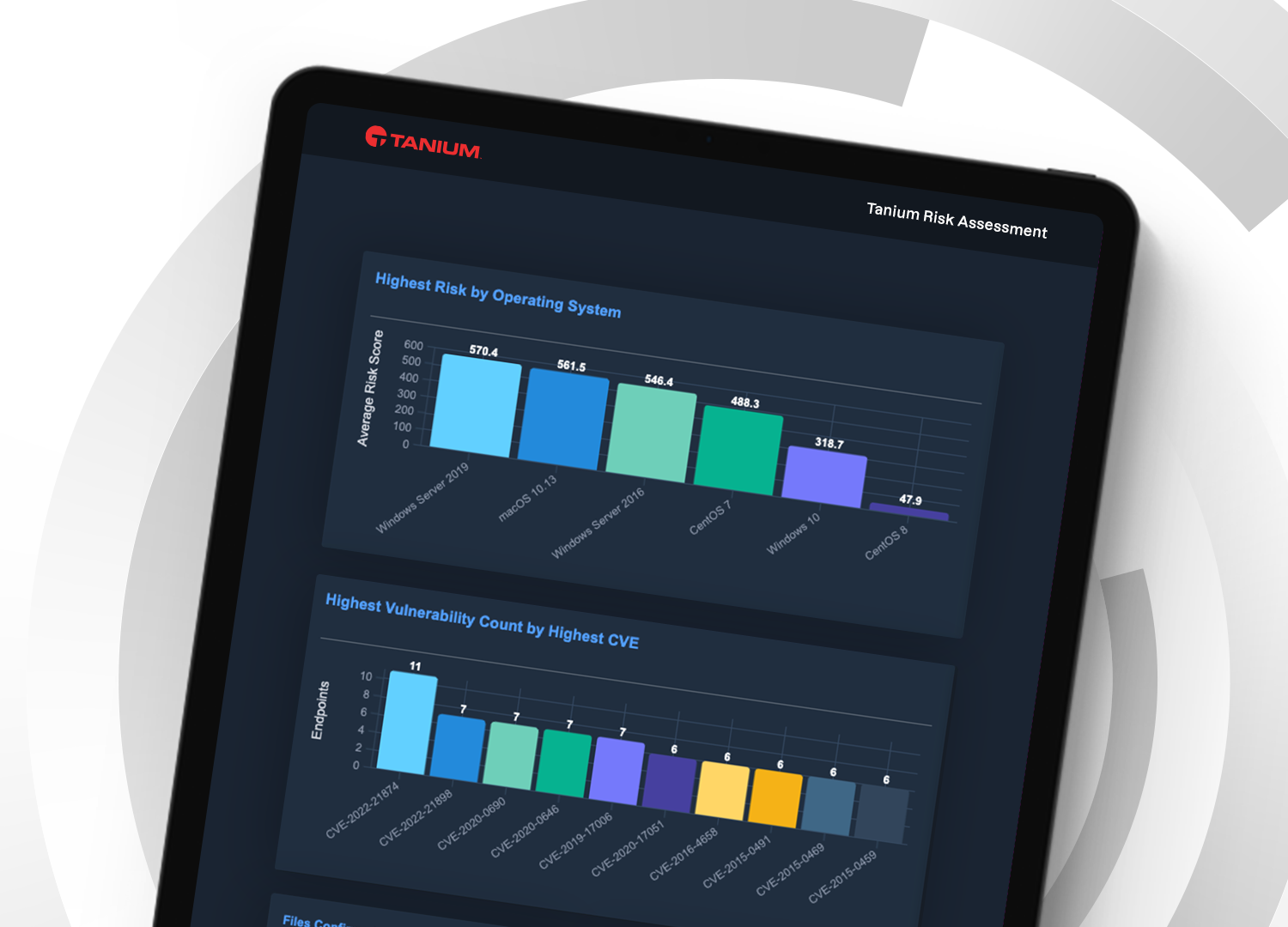
Proactive risk management starts with a comprehensive view of risk posture
The risk assessment provides dynamic scoring for each endpoint device against multiple vectors as well as an actionable improvement plan.
Actionable risk plan
Proactively communicate and improve your risk posture with an executive summary, composite risk score, asset inventory, proposed implementation plan, and Log4j exposure analysis.
Risk vector analysis
Understand your risk posture by diving into system vulnerabilities, system compliance, lateral movement assessment, sensitive and protected data exposure, insecure transport security protocols, and encryption and mutual authentication.
Compensating controls & asset criticality
Discover and measure endpoints without controls, such as credential guard, endpoint hardening, antivirus/antimalware and more. Understand criticality level assigned to the assets within the scope of the assessment.
Cyber hygiene metrics
Answer basic questions about asset inventory, patch status, and risk exposure to vulnerabilities. See what applications are running in your environment and what software you are not actually using.
Every 11 seconds there is a ransomware attack
Attacks against critical infrastructure, private companies and municipalities are becoming more frequent and pervasive. With Tanium, you can manage this threat by understanding your true exposure and prioritizing remediation with the highest impact.
0
ransomware paid in 2021
0
of discovered vulnerabilities were high- or critical-risk
0
mean time to remediate a system with critical risk
0
agree leadership should be more concerned about cybersecurity
Get started on your risk assessment
As your organization grows and becomes more distributed, you lose visibility and control of your IT environment.
Tanium can help.
Sign up below
and a Tanium Technical Solutions Engineer will get in touch with you.
Deploy our lightweight agent
and start assessing your overall risk posture across endpoints.
Begin data collection
as our Technical Solutions Engineer collect the required metadata for the risk assessment report.
Receive final report
delivered along with a prioritized list of recommendations to assist in reducing and ultimately eliminating risk contributing factors.
Request your risk assessment
Your customized risk report will include an executive summary, your risk score, proposed implementation plan, asset inventory, risk vector analysis, Log4j exposure analysis and more.
- Source: Recorded Future
- Source: Forbes
- Source: Forbes
- Source: Harvard Business Review